
Explore a variety of STEAM activities with Brainspace in honour of National STEAM Day on November 8th!
Join us to celebrate 5 days of STEAM with tons of STEAM activities each of the five days this week! View all our blogs for this week here:
Day 2: Tech (3 articles/activities)
Crypto
A bit of money history:
In the early 1900s, a culture of people that lived in Micronesia called the YAP, used a form of money called Rai stone. These big circular stones could get pretty massive and weigh up to four tons. Not something the average person could carry in a wallet! Instead, they documented who owned any part of the Rai stones.
One day, sailors were transporting a large Rai stone that fell off their vessel and sank to the bottom of the sea. Upon telling the YAP, they said, “Well okay, we know that you had it, and it still exists, so it’s still valuable.” The Yapese then documented and added its value to their list of traded currencies. Even though the stone was at the bottom of the sea, and couldn’t be seen or touched, it was still part of the Yap’s economy.
We decide what money looks like:
Money is about the exchanges that we have with each other. If we say that gold is valuable, it is. Cocoa beans, stones, and plants have all represented forms of currency in human history.
Today, Rai stones are still a part of the Yap’s economy. Unusual? Not really. Consider that most of our money is digitally documented, traded and exchanged without any paper money or coins exchanging hands. It’s an unseen value.
What is cryptocurrency?:
Cryptocurrencies, like Bitcoin, are digital currencies. The world of cryptocurrency is based on specialized mathematics called cryptography. Cryptography is the study of secret or secured communication. A cryptographer searches for, and creates code with two very important things in mind:
• highlighting information so that it can be visible in very plain sight
• verifying a piece of information’s source.
How is cryptocurrency tracked?:
Blockchain. Think of blockchain as a giant sheet of internet paper called a ledger, that records transactions. Anyone who makes a transaction gets their own sheet of paper with a record of all the other transactions being made. Once a transaction is recorded, it cannot be changed or hacked.
All who transact can see and access the ledger, but nobody – no banks or institutions – can control it. Because blockchain is a ledger system for currency, it can track value of work by artists, musicians, and writers. It can also verify the source of a transaction or “ownership.” This is important where corrupt governments have been known to steal land from people. Paper documents or “deeds” for purchase of land can be torn or burned to destroy proof of ownership. A blockchain transaction of land transfer is secure. In many ways, blockchain can keep accountability and fairness in check.
Where does Bitcoin come from?:
Miners. In the same way, we mine for gold, we mine for cryptocurrency. Cryptocurrency miners are computer users who look for “wins.” A win is when a very hard digital puzzle is solved by a computer. It’s sort of like hitting a jackpot: imagine if a series of dice were rolled and they all landed on the same number. Miners use high-powered computers that find and identify a highlighted “fact or truth” about a particular block of information. When this is discovered by the miner, it’s a win and a crypto coin is earned.
Bitcoin was created in 2009 and today, cryptocurrencies like Bitcoin and Ethereum have financial value. Bitcoin is being used in restaurants and for purchases in more places because people – not banks and governments – have decided that cryptocurrency has value. That is pretty cool.
Just like the Internet changed the way we communicate, programmable money – like cryptocurrency – will change the way we pay and decide on value.
How to Create Secret Spy Code
Not all coding is one on a computer. Codes can be created on graph paper. A substitution cipher is an easy way to begin learning about how to use and make secret codes. Whether you want a secret way to talk to your friends, or you’re just interested in creating your own, ciphers are a lot of fun to learn about and create for yourself.
So, how do you build a cipher, and what can you do with one?
To start, let’s take a look at a very simple cipher you can create in a few minutes: a simple substitution code.
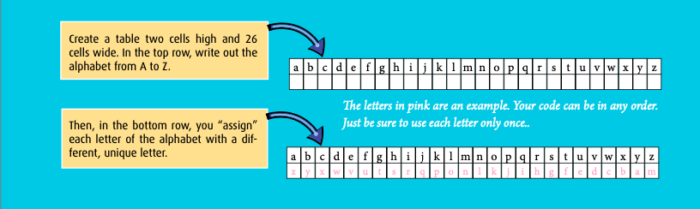
First, you begin by creating an alternate alphabet. This is done by creating a table two cells high and 26 cells wide as in the table above. In the top row, write out the alphabet from A to Z. Then, in the bottom row, you “assign” each letter of the alphabet with a different, unique letter. For example, if you write down A, B, C and D in the top row, you can then write S, E, Z, and R underneath each of those letters in the bottom row.
Make sure none of the letters share a substitution (both A and G being assigned to S, for example) or else translating your code will get very confusing! When you complete this from A-Z, you’ll have a normal alphabet above a scrambled one. This is your cipher! Now, spell words using your cipher alphabet instead of the normal one. Give everyone your secret message and the cipher table you’ve created.
If you create a message with the scrambled alphabet, people with the solution for it can match it back to the regular alphabet and decipher the code. For instance to write the word BAD, check the table we created above. We have Y assigned to B, Z assigned to A, and W assigned to D. So, instead of writing BAD, we can instead use our ci- pher and write YZW by using the table. The sentence “a bad dad” through this cipher becomes the unreadable “z yzw wzw.”

Art Code
Coding is fun. The focus and precision required to write code is a valuable learned skill.
Learn with a fun and easy coding program courtesy of codeguppy.com. Visit the site and type in the JavaScript program as you see it below. See the helpful TIPS section to help you successfully draw the sailboat.
Scan this image below using the Zappar app:
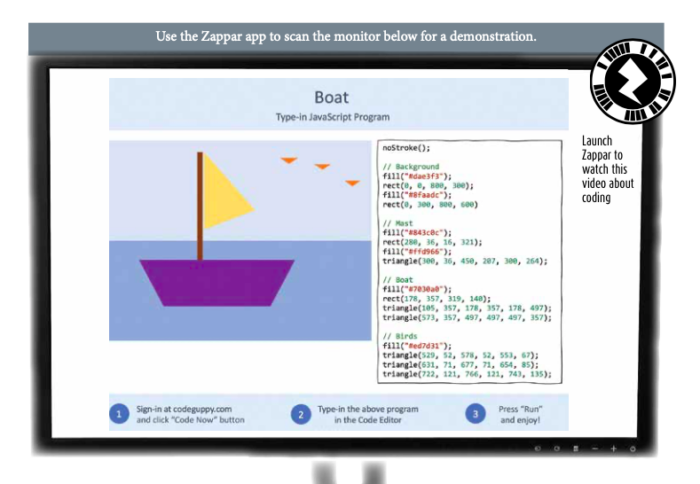
How it works:
These programs are drawings on a canvas. The canvas is made up of many small dots that you can turn black or white or even colour through code. These dots are called pixels. In a sense, the canvas is like graph paper, with each grid square being a tiny pixel on the canvas. The canvas used by Codeguppy programs is 800 pixels wide by 600 pixels tall.
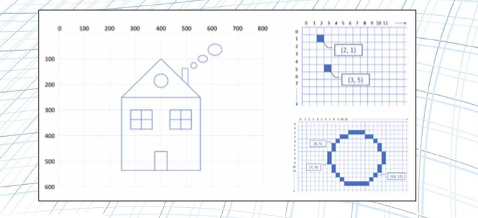
Tips:
Typing in programs from a piece of a paper is a great way to learn about coding. Since typing in the program requires attention to details, you develop focus and other useful skills beyond coding.
Here are a few tips to ensure programs are typed in correctly:
-
Type in each program very carefully exactly as it appears on the facing page. Do not skip any
letter, number or punctuation.
-
Programs are case sensitive. Please type in all of the commands using the exact case (capital letter or lower-case letter) as it appears on the paper.
-
Run the program at the end of every few lines of code. Running the program often prevents the accumulation of errors. Simply press the big “Run” button in the top-right of the code editor.
-
If there is an error, check the typed-in program against the program on the paper.
